
|
||
|
SecureMyi.com Security and Systems Management Newsletter for the IBM i
April 9, 2014 - Vol 4, Issue 6
|
||

|
||
|
SecureMyi.com Security and Systems Management Newsletter for the IBM i
April 9, 2014 - Vol 4, Issue 6
|
||

|





|
The Reality of User Limited Capabilities LMTCPB(*YES)By Dan Riehl In speaking to many security analysts over the years, it is obvious that there is a BIG Disconnect on what the "Limited Capabilities" attribute of the user profile actually does. In this article, I hope to dispel these potentially dangerous misconceptions. In this April 9, 2014 issue of the SecureMyi Security Newsletter, the featured YouTube Video presents a video discussion of this important topic. What IS Limited Capabilities?System users can gain access to the IBM i shell command line through various IBM-supplied screens, including most IBM menus, the Work with Spooled Files (WRKSPLF) command display, the Work with User Jobs (WRKUSRJOB) command display, and numerous other commands and facilities. Allowing users to access a command line can be very dangerous; for example, you don't want users running commands like DLTF CUSTOMER, which would delete your Customer file. A user who has command line access can run any CL command that he or she is authorized to run at the command line interface. IBM allows you to control the ability of a user to run CL commands at a command line by specifying the LMTCPB(Limit Capabilities) attribute of the user profile. To create a user that has limited command line capabilities, you use the CRTUSRPRF(Create User Profile) command as shown here: CRTUSRPRF... LMTCPB(*YES) The common misconception regarding users with limited capabilities( i.e. LMTCPB(*YES) ) is that we think that these users cannot run any ad-hoc CL command, such as WRKSPLF or DLTF CUSTOMER But, in reality, a user with limited capabilities CAN run CL commands using several methods which we will discuss in this article. Did you know that IBM ships certain CL commands with a special command attribute that specifies that Limited Capability users are allowed to run the command at a shell command line. These commands include:
The Command Attribute ALWLMTUSRYou can examine the command definition of a CL command using the command DSPCMD(Display Command). To examine the command DSPMSG(Display Message), you could use the following command. DSPCMD DSPMSG On the resulting display you will see that the command attribute named ALWLMTUSR (Allow Limited Users) is set to the value *YES. This setting means that the DSPMSG command can be used by Limited Capabilities users from the command line. All of the commands in the list above are shipped from IBM with the value ALWLMTUSR(*YES). Generally, all other CL commands are shipped as ALWLMTUSR(*NO), prohibiting the use of the commands at the command line by Limited Capabilities users. Each CL command contains the ALWLMTUSR attribute, but almost all commands have the attribute set to *NO, meaning "Do Not allow Limited Capabilities Users to run the command at a command line." This is the system's default value for all newly created commands. But, as a system administrator, you can change any CL command that can be run at the command line to allow limited users to also run the command at the command line. This change is accomplished using the CL command CHGCMD(Change Command), as in the following example: CHGCMD CMD(WRKSPLF) ALWMLMTUSR(*YES) Running this command changes the IBM supplied CL command WRKSPLF(Work with Spooled Files) to allow Limited Capabilities users to run this command at a command line. Often third-party software will install new CL commands that are set to allow limited users to run the commands with ALWMLMTUSR(*YES). It's wise to examine any newly created commands to make sure that limited users cannot run the new commands. Finding CL Commands that are Allowed for Limited Capability UsersCarsten Flensburg recently contributed an article for the SecureMyi Security Newsletter in which he presented his custom CL command WRKCMDSEC(Work with Command Security), which among other useful functions, will search out and list any commands that are not set to ALWMLMTUSR(*NO). The Article and the source code can be found in the February 12, 2014 issue. Remote Commands Don't Honor the Limited Capability User SettingIn addition to being able to run CL commands that specify ALWLMTUSR(*YES), a user can run ANY CL command he or she is authorized to run by using the IBM i Access for Windows Remote Command facility. From a PC command prompt, the user can run any authorized CL command using the MS/Windows executable Remote Command(rmtcmd.exe) which is installed with IBM i Access for Windows. The rmtcmd.exe is the MS/Windows client executable that interfaces with the IBM i Remote Command Host Server. Figure 1 below shows an example of a user with Limited Capabilities(*YES) running a CL command using rmtcmd.exe (in red) and the Remote Command Host Server's response to the CL command being run(also in red). In this case, the CL command CRTLIB(Create Library) is set to NOT allow Limited Users to run the command, but rmtcmd.exe doesn't care.
Figure 1 Running a CL command via rmtcmd.exe in IBM i Access for Windows 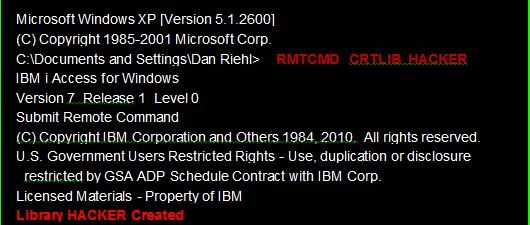
In this example, a user with Limited Capabilities has just run the CRTLIB(Create Library) command to create the HACKER library. The rmtcmd.exe completely ignores the Limit Capabilities attribute of the user profile and therefore allows any user to run any command he or she is authorized to run. Since the rmtcmd.exe is installed on PCs when installing IBM i Access for Windows, and since it is an integral part of the package, the activity of the Remote Command Host Server must be logged and controlled using a server Exit Program. For information on using Exit Programs to log and control this type of activity, see my article on Invisible Data Theft in the March 26, 2014 Issue. Using an Exit program would allow you to reject this type of activity, and log the attempted breach of your system security. Commands run through SQL/ODBC Don't Honor the Limited Capability User SettingAnother method that can be used to run ad-hoc CL commands by users with Limited Capabilities is through ODBC using a remote program call, as in: CALL QCMDEXC ('DLTF MYFILE' 11) QCMDEXC is a documented IBM supplied API that processes CL command requests. As you can see, this program is invoked by sending parameters containing the CL command to execute and the command length. Here a Limited Capabilities user deletes the file named MYFILE. This SQL/ODBC activity can also be logged and controlled using Exit Programs. The Take AwaysThe Limited Capabilities attribute of the User Profile is NOT a restriction on running ad-hoc CL commands. It limits only which CL commands a Limited Capabilities user may run at a command line. The ALWLMTUSR(*YES) attribute of a CL command allows the command to be run from a command line by a Limited Capabilities User. So, you must check all your commands to be sure you know which commands are allowed; and do this check periodically. I saw one system in which the FTP command had been changed to be Allowed for Limited Users. Don't only check the CL commands in QSYS. YOU have numerous other commands. Use the custom command WRKCMDSEC to locate all CL commands that are Allowed by Limited Capability Users. The CL commands of Limited Capabilities users are only limited by the user's permissions when using tools like rmtcmd.exe or an ODBC call to QCMDEXC. To Log and Control the access, implement Exit Programs. There are numerous vendor Exit Program products out there to choose from. Just make sure you are getting a package that can log and control this type of activity, along with working with the myriad of other network servers on your IBM i. All Application End-Users should have their User Profile set to LMTCPB(*YES).
About the Author 
Dan Riehl is the Editor of the SecureMyi Security Newsletter and a Security Specialist for Dan performs IBM i security assessments and provides security consulting, remediation, forensic evaluations, and other customized security services for his clients. He also provides training in all aspects of IBM i security and other technical areas through The 400 School, Inc. 
|

|
|