
|
||
|
January 4, 2012 - Vol 2, Issue 1
|
||

|
||
|
January 4, 2012 - Vol 2, Issue 1
|
||

|


|
The IBM i Intrusion Detection SystemBy Dan Riehl How do you know if someone is scanning your IP ports for vulnerabilities? Or how do you know if you're being attacked by denial of service attacks like a SYN Flood or Smurf attack? The IBM i Intrusion Detection System (IDS) alerts you when an attack against the system is in progress. In most cases, you have no other way to monitor for these intrusion events. With IBM i version 6.1 and 7.1, you can have the IDS up and running in a few minutes. IBM i Navigator for Windows provides an IDS Setup Wizard, which makes setting up the IDS a very simple process. On my system, I had it up and running in about 30 minutesó25 of those were spent reading the documentation and the On-Line help text. Why do I need an Intrusion Detection System?An IBM i connected to any network should be running the IDS. Some may say they're protected behind a corporate firewall and therefore are immune to these types of attacks. But attacks also come from inside your network, and as far as outside attacks, do you want to bet the security and availability of your System that the firewalls can reject ALL unwanted traffic?
Each host system needs to be the final arbiter of who and what has access to the system resources. You cannot disregard the security of the IBM i simply because you have a firewall. In most cases, it's the IBM i in your data center that manages and protects the critical company jewels. It's the system that stores the very sensitive data that you must protect. Setting up the IDS on your IBM i just makes sense. When an attack occurs, instant notification of the attack can be sent to a message queue as well as via email to several email addresses you stipulate. When you see an incoming attack, you can then take preventative actions to stop the attack or prevent the attacker from getting to you again. As prevention, you can set packet filtering rules within IBM i Navigator and adjust firewall rules as needed. The IDS is a detection system; it, alone, cannot prevent an attack. In addition to monitoring for attacks, the IDS also detects if the IBM i is being used as the attacker of another system. You would certainly want to know if someone is launching an attack from within your system. IBM i 6.1 and 7.1 Differences from 5.4Since OS/400 V5R4M0, IBM i has included the IDS that monitors network activity for numerous types of attacks. Under V5R4M0, setting up the IDS is a difficult and frustrating exercise. But as of IBM i 6.1, and the introduction of the IDS Setup Wizard, configuring the IDS has become a very simple process. The dependency on the Quality of Service (QoS) Server in V5R4M0 has been removed. The QoS server integration was my biggest stumbling block in that older implementation. I just could not get it to work. The remainder of this article will focus on the IDS in IBM i 6.1 and 7.1. If you're still at 5.4, you can configure the IDS using the instructions in the IBM Redbook IBM i5/OS Intrusion Detection System at http://www.redbooks.ibm.com/redpapers/pdfs/redp4226.pdf Configuring the IDS for IBM i 6.1 and 7.1Running the IDS requires that you set up the System Security Audit Journal QAUDJRN and that the system value QAUDCTL contains the value *AUDLVL. When you start the IDS through the IBM i Navigator option, the value *ATNEVT is automatically added to the system value QAUDLVL, or QAUDLVL2. This specifies that the system is to audit the Intrusion Events, referred to as Attention Events. Using the IBM i Navigator Intrusion Detection Setup Wizard, you can configure and start the IDS in no time. In Navigator, you access the Intrusion Detection System under the Security tab. From the IDS tab, you can right-click and select to Start, Stop, Manage Policies, View IDS Events, and Set IDS Properties, like alert email addresses and message queues. When you select to manage policies, the IDS Policy Wizard walks you through the entire setup process. You can select to set Policy for Attacks, Scans, and Network Traffic. Here's the Navigator screen for setting Attack policy for different attack types. 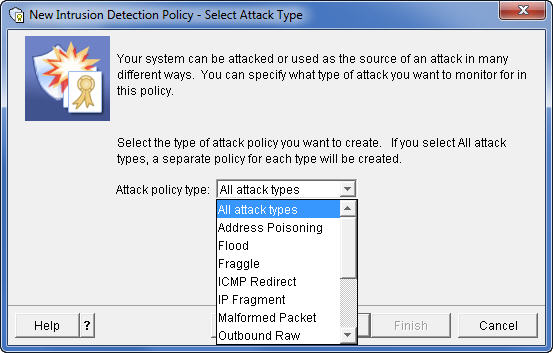
The system comes with a default policy configuration. Just select to Set Up Policy for each category, (Attacks, Scans, Traffic) and click Next, Next, Next until you are done. If you find you're being alerted for insignificant events, you can change the policy at any time. Starting and Testing the IDSOnce the IDS policies are set, right-click on the IDS in Navigator and select the Start option to start the IDS. You'll need a few tools to test your IDS. I used SuperScan, one of McAfee's Free Tools, and the Windows version of Nmap, a free security scanner. These tools allow you to perform various scanning tests on a system. You can try additional tools and tests as well. You can find a plethora of security tools at http://sectools.org. Reviewing the IDS EventsAfter you've run a few tests against your system, right-click on the IDS in Navigator and select View IDS Events. If you've caught some IDS events, you get a screen that looks similar to the following figure. Note: For confidentiality, I have masked my IP address that is listed in the report. Those are the solid black boxes. 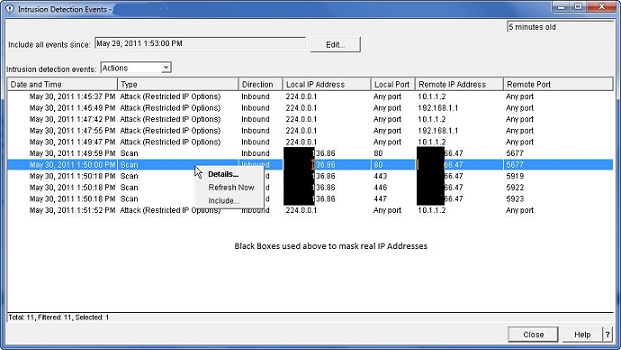
When you right-click on an intrusion event, you can display the details of the event. In this example, there are some attack events and some scan events that were detected. You can see the originating IP address. Selecting Details will show the content of the IP packet that was recorded. For each event recorded, a message is optionally sent to a message queue and also sent to up to three email addresses. The content of the message contains the detail of the intrusion event. In a real attack on your system, you can use Navigator to edit the IP Packet Rules to specify what should be done when packets from the attacking IP address arrive on your system. You might also want to use other tools like TraceRoute (CL command TRACEROUTE or MS/Windows command TraceRT) to determine the location of the originator of the attack. IBM IDS DocumentationHere are some IBM publications that explain the IDS and can help you build your IDS policies: The IBM Information Center topic on using the Intrusion Detection System IBM i - Security Intrusion Detection Manual 6.1 (PDF Download) IBM i - Security Intrusion Detection Manual 7.1 (PDF Download) About the Author  Dan Riehl is the Editor of the SecureMyi Security Newsletter and a Security Specialist for
Dan Riehl is the Editor of the SecureMyi Security Newsletter and a Security Specialist for the IT Security and Compliance Group, LLC. Dan performs IBM i security assessments and provides security consulting, remediation, forensic evaluations, and other customized security services for his clients. He also provides training in all aspects of IBM i security and other technical areas through The 400 School, Inc. 
|

|

|